 Consider the following implementation of an algorithm for
finding the greatest common divisor of two integers:
Consider the following implementation of an algorithm for
finding the greatest common divisor of two integers:
int gcd(int a,int b) {
if (a == b) return a;
if (a > b) return gcd(a-b,b);
return gcd(a,b-a);
}
The C compiler has compiled this procedure into the following code
for an unpipelined Beta processor:
gcd:
PUSH (LP)
PUSH (BP)
MOVE (SP, BP)
PUSH (R1)
PUSH (R2)
LD (BP, -12, R0)
LD (BP, -16, R1)
CMPEQ (R0, R1, R2)
BT (R2, L1)
CMPLE (R0, R1, R2)
BT (R2, L2)
PUSH (R1)
SUB (R0, R1, R2)
PUSH (R2)
BR (gcd, LP)
DEALLOCATE (2)
BR (L1)
L2:
SUB (R1, R0, R2)
PUSH (R2)
PUSH (R0)
BR (gcd, LP)
DEALLOCATE (2)
L1:
POP (R2)
POP (R1)
MOVE (BP, SP)
POP (BP)
POP (LP)
JMP (LP)
???
0x00000594
0x00001234
0x00000046
0x0000002A
0x0000000E
0x0000001C
0x00000594
0x0000124C
BP-->0x0000002A
0x0000000E
SP-->0x00001254
0x0000000E
What is the value of the second argument ("b") to the current call to gcd?
= 0x124C + (6 words = 24 bytes = 0x18 bytes)
= 0x124C + 0x18
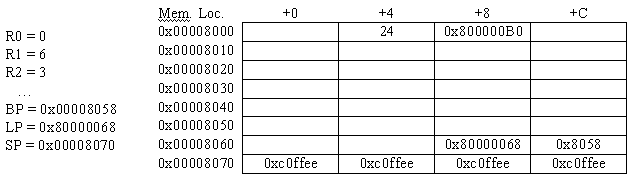 The contents of the blank table entries are unknown.
The contents of the blank table entries are unknown.