Electronic Commerce and Intellectual Property:
Web of Trust
Branko J. Gerovac and David C. Carver
a white paper presented to "Technology-Based Intellectual Property
Management"
A Forum Organized by the Interactive Multimedia Association
in cooperation with the U.S. Copyright Office
March 7, 1996
Center for Technology, Policy and Industrial Development
Massachusetts Institute of Technology
As we publish and distribute material electronically, it is too easy to get wrapped up in technology and forget that the real purpose in the business of distributing material is to maximize income[1]. There is strong initial temptation to use technology to protect intellectual property by controlling access to material. This has been true whether the material is print, pictures, audio, video, or combinations. The intent of the protection is to insure proper payment is received for the use of material and to prevent unauthorized use. Unfortunately, attempted barriers to unauthorized use become burdensome barriers to the legitimate user.
The attempt at protection can take several forms, such as, limiting distribution to specific locations on a communications network and then restricting access to those locations, or encrypting the material and carefully managing access to decryption, or marking the material (e.g., digital watermarks) to enable tracking of illegal use and distribution. This is not to say that protection mechanisms are not important in some circumstances. Some material benefits from constraining its distribution, for example, personal information such as health records, proprietary information, and differentially priced information such as market research reports. But, these situations are inherently limited distribution and not mass media publishing.
From a technology perspective, there needs to be a distinction between property protection/policing functions and billing/payment functions. Many electronic commerce systems currently being proposed intermingle the two. Policing mechanisms incur an overhead cost in processing, storage, and communication. The mechanisms offer only relative, not absolute, protection. All mechanisms can be circumvented given sufficient motivation, for example, if the perceived intrinsic value of the material is greater than the inherent cost of breaking the encryption.
Electronic publishing and distribution would benefit more by making it easier to bill and pay for material[2]. Electronic commerce systems do not yet approach the full flexibility and utility of conventional commerce. Most existing and proposed systems can be characterized as either a two party model (e.g., online services such as Lexus/Nexus or CompuServe), where the single provider brokers access to material, or a three party model (e.g., NetBill, Cybercash), where the broker settles the transaction between the publisher and the consumer.
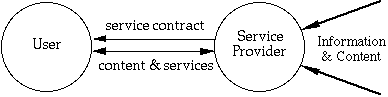
In the two party model (Figure 1.), when you subscribe to a service, you usually sign a service contract to signify your compliance with a sets conditions concerning use of the service and any materials acquired therein. Online services, which existed prior to the commercial Internet availability, tend to be dialup oriented (non-networked) and built upon on a variety of proprietary protocols and facilities. Billing and payment is done off-line. Property protection is approached by controlling access to material through restricted distribution.

Figure 1. - Two party model
The three party model (Figure 2.) offers the ability for consumers to get material directly from publishers anywhere on the net and the ability to pay for the material electronically. While the material is not brokered, the transaction is. This approach promises to police electronic commerce through the use of technology. Encryption and authentication technology are used to achieve hard guarantees in a fully committed transaction.
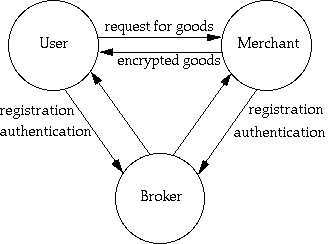
Figure 2. - Three party model.
Both of these models effectively partition the market to those publishers and consumers directly known to the broker -- this is an advantage to the broker, but not the publisher or consumer. Thus they create closed domains with confined benefits. For example, if you read a magazine article and pass it on to a friend who you think would be interested, if they are not registered with the broker, there is no easy way for them to pay for their use of the article -- non-compliance is easier than compliance.
What is missing is an open multiparty model (Figure 3.), which promotes voluntary compliance, leverages existing practice, contract and copyright law, and civil and financial systems. Thereby, electronic commerce could mirror the conventional web of trust among consumers, publishers, and brokers. The key technology then is not encryption, but rather is how to attach information that describes permissible usage, the charges for that usage, how to make payment, and perhaps how to inquire about uses not listed. This information then becomes part of the material (perhaps along with other information) and moves with the material in the communications network[3] - for example, a "tear off" bill that can be handed your bank to be paid.
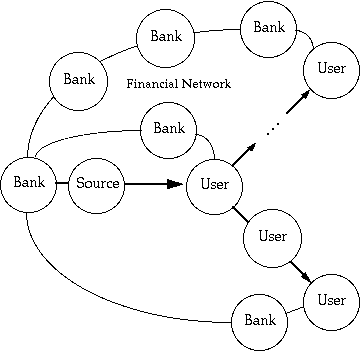
Figure 3. - Open multiparty model.
In essence, this would redirect the focus of electronic commerce away from erecting barriers by protecting bits and toward easing distribution and payment.
Revenue is best protected by providing material that has value to customers, is priced appropriately, and where it is easy to comply with usage and billing.
The publishing industry (large and small, across media) is facing a dilemma. Success will go not to those who erect barriers and partition markets, but to those who figure out how to take advantage of the ease of electronic copying, distribution, and commerce.
For further information, email: bjg@mit.edu or dcc@mit.edu.