Note that these 3-part structures bear some similarity to the 3-part structures in RDF or the Symantic Web:
Person Function Qualifier The person who is authorized to do something (identified by the person's Kerberos principal) The action the person is permitted to do (also could be a role the person has or a collection of actions or responsibilities) The unit or area within which the person can perform the Function. This could be an HR org unit, financial object, or some other unit
Subject + Verb + Object
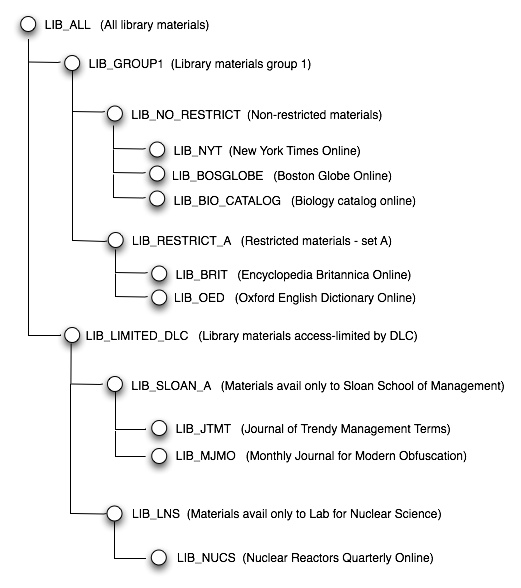
Each node and leaf in the diagram represents a Qualifier, each with a code (e.g., LIB_ALL, or LIB_GROUP1) and a name ("All library materials", or "Library materials group 1").
Further, suppose that the following Authorizations for access to Library materials have been explicitly created:
Function name Description ACCESS LIBRARY MATERIALS Allows a person to view specified online library materials ADMIN ACCESS TO LIB MATERIALS Allows a person to set or change access permissions to Library materials
Person Function Qualifier JOEUSER ACCESS LIBRARY MATERIALS LIB_GROUP1 FREDUSER ACCESS LIBRARY MATERIALS LIB_GROUP1 RMURDOCK ACCESS LIBRARY MATERIALS LIB_BOSGLOBE RMURDOCK ACCESS LIBRARY MATERIALS LIB_MJMO EINSTEIN ACCESS LIBRARY MATERIALS LIB_LNS NBOHR ACCESS LIBRARY MATERIALS LIB_LNS LTHUROW ADMIN ACCESS TO LIB MATERIALS LIB_SLOAN_A BSMITH ADMIN ACCESS TO LIB MATERIALS LIB_LNS
Examples of "Relations" - data about people Person or agent Relation-function Object aka Subject aka Verb aka Object REPA STAFF - ADMINISTRATIVE IS&T FRED STUDENT - GRAD CHEM JIMB FACULTY - RETIRED EECS LTHUROW FACULTY - MIT SLOAN AJJONES HAS COMPLETED CLASS 8.232 Relative Quantum Field Theory I
Groups of relation-functions related to people's student or staff status Function Group Name Description Qual
typeLinked Function name CURRENT MIT PERSON SET L1 Current MIT people statuses for access to most Library materials DEPT FACULTY - MIT FACULTY - VISITING NON-MIT CROSS-REGISTERED STAFF - ACADEMIC STAFF - ADMINISTRATIVE STAFF - POSTDOC STAFF - SUPPORT STAFF - VISITING RESEARCHER STUDENT - GRAD (CONF) STUDENT - GRADUATE STUDENT - UNDERGRAD (CONF) STUDENT - UNDERGRADUATE RETIRED FACULTY/STAFF Retired faculty and staff members DEPT FACULTY - RETIRED STAFF - RETIRED
Columns in a definition of a Rule of type 2b Condition function or function-group Condition object Implied auth function Implied auth qualifier If a person has a "Relation" with this function... ...and this object, or a child/grandchild/etc. of this object ...then the person gets an implied authorization for this Function... ...and this Qualifier
| Rule ID | Rule name | Where a person has a role/relation for function shown below and the qualifier is either the object shown below or a descendant of the object... | ...give the person an implied authorization for the function and object shown below. | |||||
|---|---|---|---|---|---|---|---|---|
| Cond Function | Cond obj type | Cond obj code | Result function | Result obj type | Result obj code | |||
| 19 | People (set L1) can access lib materials (Group 1) | CURRENT MIT PERSON SET L1 | Depart- ment |
D_ALL | ACCESS LIBRARY MATERIALS | Library material |
LIB_GROUP1 | |
| 20 | Retired faculty/staff can access limited lib materials | RETIRED FACULTY/STAFF | Depart- ment |
D_ALL | ACCESS LIBRARY MATERIALS | Library material |
LIB_NO_RESTRICT | |
| 21 | Sloan School people can access special set of lib materials | CURRENT MIT PERSON SET L1 | Depart- ment |
D_SLOAN | ACCESS LIBRARY MATERIALS | Library material |
LIB_SLOAN_A | |
Person has this "Relation"... ...and after applying the rules, the person gets this implied authorization. Person Relation-function Relation
ObjectPerson Resulting
Authorization
FunctionResulting
Authorization
QualifierREPA STAFF - ADMINISTRATIVE IS&T REPA ACCESS LIBRARY MATERIALS LIB_GROUP1 FRED STAFF - ADMINISTRATIVE IS&T FRED ACCESS LIBRARY MATERIALS LIB_GROUP1 JIMB STAFF - ADMINISTRATIVE IS&T JIMB ACCESS LIBRARY MATERIALS LIB_NO_RESTRICT LTHUROW STAFF - ADMINISTRATIVE IS&T LTHUROW ACCESS LIBRARY MATERIALS LIB_NO_RESTRICT LTHUROW STAFF - ADMINISTRATIVE IS&T LTHUROW ACCESS LIBRARY MATERIALS LIB_SLOAN_A