| Vol.
XXVIII No.
1 September / October 2015 |
| contents |
| Printable Version |
Why MIT Is Implementing
Duo Two-Factor Authentication
Beginning October 1, 2015, MIT faculty, staff, and affiliates will need a second authentication factor for access to MIT systems where sensitive data are stored. These include systems accessed through the Touchstone authentication service, systems managed by Information Systems and Technology (IS&T), and systems located within IS&T data centers, as well as systems accessed through the MIT Virtual Private Network (VPN). Duo authentication will be required from wherever you connect, whether via direct connection to MITnet, VPN, or from a remote address.
Why is two-factor authentication (2FA) important?
When it comes to online authentication, passwords are now a weak link. This is as true at MIT as anywhere. For example:
- Some users choose weak (i.e., easy to guess) passwords. There are well-known databases of common passwords that are used by adversaries to break into accounts.
- Some users use the same passwords on different systems or Websites. This means that an adversary who steals the password database from some not-very-important Website can look for @mit.edu accounts, and try to log into that MIT account using the same password.
- Some users fall for phishing attacks – for example, responding to an email that pretends to be from an administrator asking for your password, or accidentally mistyping a Website's URL and typing your password into a Web page controlled by a hacker. This, again, allows the bad guys to gain access to an MIT account.
One common example of this has the use of phishing email to obtain end-user credentials for attacks against direct deposit payroll systems. These attacks have been successful against a number of MIT's peer institutions, including BU and Duke University. MIT has seen these attacks as well, although the Institute has not been targeted as aggressively as some other universities.
Increases in computing power, the rapidly expanding inventory of viruses and other types of malicious code, and keystroke loggers have also made it easier for hackers to obtain passwords.
On top of these vulnerabilities, there’s another major concern. Users may not know for long periods of time that their passwords have been compromised. A hacker logging in with a compromised password merely shows up within security logs as a successful login.
How two-factor authentication helps
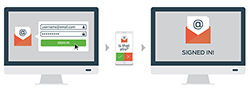
In the face of these security threats from compromised passwords, IS&T has been piloting the Duo service. Two-factor authentication is a mechanism used to protect systems, services, and accounts for which a password alone provides insufficient security. It is based on the principle of something you know (your username and password) and something you have (your smartphone, landline, or a hardware token). Users are first prompted to authenticate with their username and password; they are then prompted for a second authentication step using their phone or a token.
For convenience, Duo allows users to “remember” their browsers for 30 days, so that the second factor need not be entered at every login. For most use cases the increased risk associated with this convenience is small. Nevertheless, for the most secure computing experience, IS&T recommends not using the “remember” feature.
Two-factor authentication significantly raises the barrier and limits the effectiveness for all of the above attacker scenarios. Even if hackers compromise Kerberos passwords via a phishing email, malware, or other attack, they still won’t have access to the second factor, i.e., the associated smartphone, landline, or token.
Two-factor authentication can also help prevent abuse of MIT’s VPN. IS&T sees several dozen compromised Kerberos accounts used to access the VPN each month. Requiring Duo for VPN access will help prevent these attacks and increase the effectiveness of security implemented for systems and services intended to be available only to users from within MIT’s network.
Duo has been in use on a pilot basis since 2013 for Kerberos and VPN access, and was recently extended to Windows Remote Desktop, MIT’s critical infrastructure systems, and all IS&T-managed Windows servers.
| Back to top |
Support
If you’re not yet using Duo, several resources are available to help get you started. To learn how to install and use Duo at MIT, see the Duo Home Page in the Knowledge Base at kb.mit.edu/confluence/x/m9YwCQ. You may also want to check out Duo’s Guide to Two-Factor Authentication at https://guide.duosecurity.com/.
If you have a smartphone, you should use the Duo app – it’s the most convenient option (there are no numbers to type), and you will not incur SMS charges when you use the Duo service.
If you have a flip phone, you may want to use a hardware token (called a YubiKey). You can sign up for one using the Duo Token Request Form at ist.mit.edu/duo/token-request. Instructions for registering your YubiKey are available in the Knowledge Base at kb.mit.edu/confluence/x/to8wCQ.
| Back to top | |
| Send your comments |
| home this issue archives editorial board contact us faculty website |