Safe learning in robotics:
Unmanned vehicles promise to transform many aspects of our lives, including transportation, agriculture, mining, and construction. Successful use of robot autonomy in these areas depends critically on the ability of robots to adapt safely to changing operational conditions. Recent advances in machine learning have inspired a new major research direction where learning-enabled planning and control can accomplish complex tasks that had been intractable in the past. Two critical considerations for applying these techniques onboard autonomous systems remain: learning online, relying on streaming data, and guaranteeing safe operation, despite the uncertainty of learning algorithms.
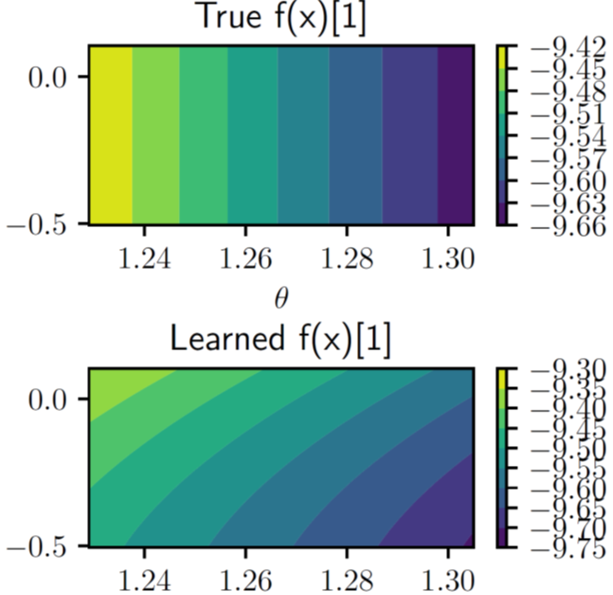
Given streaming observations of the system state, we use Bayesian learning to obtain a distribution over the robot dynamics. In turn, the distribution is used to optimize the system behavior and ensure safety with high probability.
We pay special attention to the following issues.
-
Robots operating in real-world settings must navigate and maintain safety while interacting with many heterogeneous agents and obstacles. Reinforcement learning methods have emerged recently, which directly learn actions in multi-agent settings in response to the observed environment. However, these methods provide no formal guarantees of safety. The proposed learning-enabled optimization-based controller prevents the robots from entering unsafe sets in a minimally invasive fashion by projecting desired actions to the closest safe action.
-
Safe exploratory planning is a key yet challenging problem in many engineering domains, such as Mars rover exploration and delivery drones. In context, a robot is used to explore an environment with an unknown, state-dependent disturbance function while avoiding some forbidden areas. A novel framework to solve such uncertainty-aware safe exploratory problems by combining neural control contraction metric with Gaussian process is proposed.
Related publications:
- Probabilistic Safety Constraints for Learned High Relative Degree System Dynamics
- Control Barriers in Bayesian Learning of System Dynamics
- Safe Multi-Agent Interaction through Robust Control Barrier Functions with Learned Uncertainties
- Uncertainty-Aware Safe Exploratory Planning Using Gaussian Process and Neural Control Contraction Metric
Autonomous data collection at sea for oceanographic research:
Even though the ocean is essential to maintaining life on our planet and the effects of human activity on it are significant, our knowledge of it is still limited. My research recognizes that the recent advances in machine learning, robotics, statistical signal processing, and high-performance computing can create new capabilities to explore, analyze, and sustainably manage these natural resources.
Predicting acoustic propagation at sea is vital for various applications, including sonar performance forecasting by the Navy and mitigating noise pollution at sea. The ability to predict sound propagation in bottom-limited environments depends on understanding the seabed’s geoacoustic characteristics, and inferring those characteristics from ocean acoustic measurements is known as geoacoustic inversion (GI). I am developing learning-enabled methods with attractive computational costs to characterize the undersea environment and quantify their uncertainties based on acoustic information sources. A lower computational complexity is essential to run the developed methods in real-time on the limited resources of autonomous platforms. I design active planning algorithms for marine robots to achieve information-seeking autonomous data collection at sea for oceanographic research.
Cyber-physical systems security:

The distributed nature of cyber-physical systems and cloud robotics is their Achilles' heel, as it is a source of vulnerability to cyber-attacks. We concentrate on an important class of attacks called the "man-in-the-middle" (MITM) and introduce the problem of learning-based attacks in these systems. The attacker attempts to learn the dynamics of the plant and subsequently overrides the controller's actuation signal to destroy the plant without being detected. The controller, on the other hand, is constantly on the lookout for an attack. We show how the controller can impede these attacks by superimposing a carefully crafted privacy-enhancing signal upon its control policy.
This project is a complement to learning-based approaches for control as we assume the controller has perfect knowledge of the system dynamics and tries to discover the attack from its observations. The attacker, on the other hand, attempts to learn the system and then destroy it. The assumed information-pattern imbalance between the controller and the attacker is justified since the controller is tuned for a much longer time.
Related publications:
- Learning-Based Attacks in Cyber-Physical Systems
- Authentication of Cyber-Physical Systems under Learning-Based Attacks
- Learning-Based Attacks in Cyber-Physical Systems: Exploration, Detection, and Control Cost Trade-offs
Data-driven control of quantum systems:
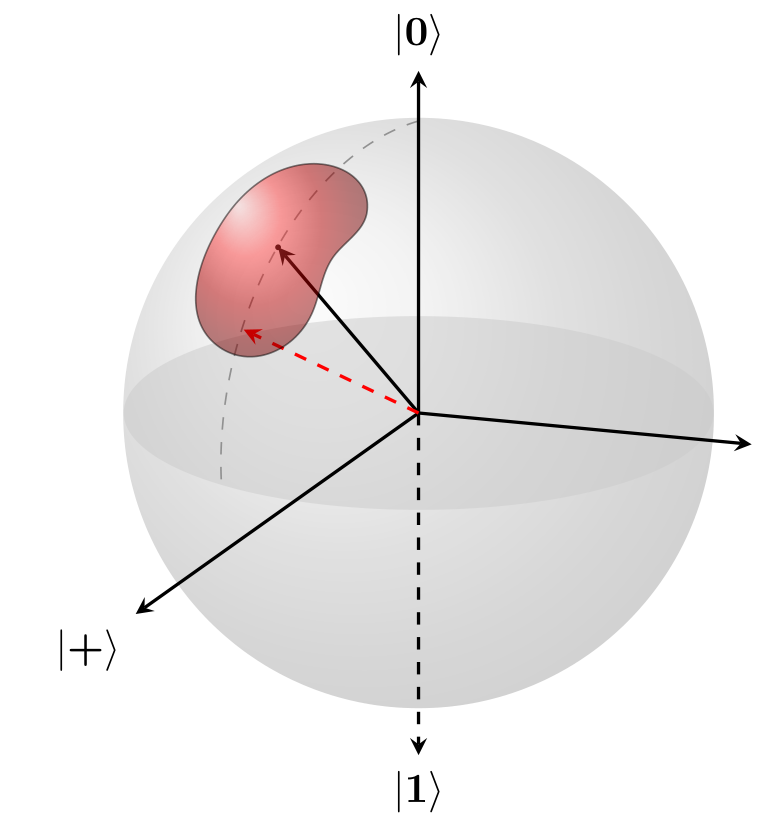
Quantum engineering is a rapidly growing field that seeks to utilize quantum dynamical systems to perform sensing, communication, or computation by exploiting the unique resources of quantum mechanics. The success of many quantum devices is dependent on precise control of their dynamics.
We attempt to bridge the gap between learning and control for quantum systems. By not relying on manually-designed models, which can be brittle, our method will account for the complexity of real-world applications. We utilize a hierarchical design that layers quantum state tomography, quantum process tomography, and Hamiltonian learning to identify the Hamiltonians. In turn, the learned Hamiltonians is utilized to formalize data-driven optimization-based quantum control techniques.
Related publications:
- Model-Predictive Quantum Control via Hamiltonian Learning
- Lyapunov Quantum Control via Bayesian Hamiltonian Learning (submitted)
Network localization and navigation:
Location-awareness is vital for the operation of wireless networks and their applications, including factory of the future (FoF), smart environments, asset tracking, autonomy, and crowdsensing. Network localization and navigation (NLN), where a network of nodes is used to aid in localizing its members, is crucial for developing mass-market services and applications in the Internet of Things (IoT) era.
We pay special attention to the following issues.
-
In applications such as ocean-of-things (OoT) or indoor positioning, due to external disturbances and obstacles, inaccuracies appear between the desired and the actual deployed position of the nodes. These position inaccuracies may also occur in adversarial scenarios, where an adversary aims to hamper the localization process of legitimate nodes by forcing them to move from their initial or desired positions.
-
Adversaries may exploit location information to perform carefully crafted attacks on cyber-physical systems. Therefore, studying and preventing such security breaches by enhancing agents’ location secrecy is vital. Location secrecy is also critical in applications such as adversarial search-and-rescue missions and pursuit-evasion in mobile robotic settings.
Related publications:
- Node Deployment under Position Uncertainty for Network Localization
- Location Secrecy Enhancement in Adversarial Networks via Trajectory Control
Communication in cyber-physical systems:
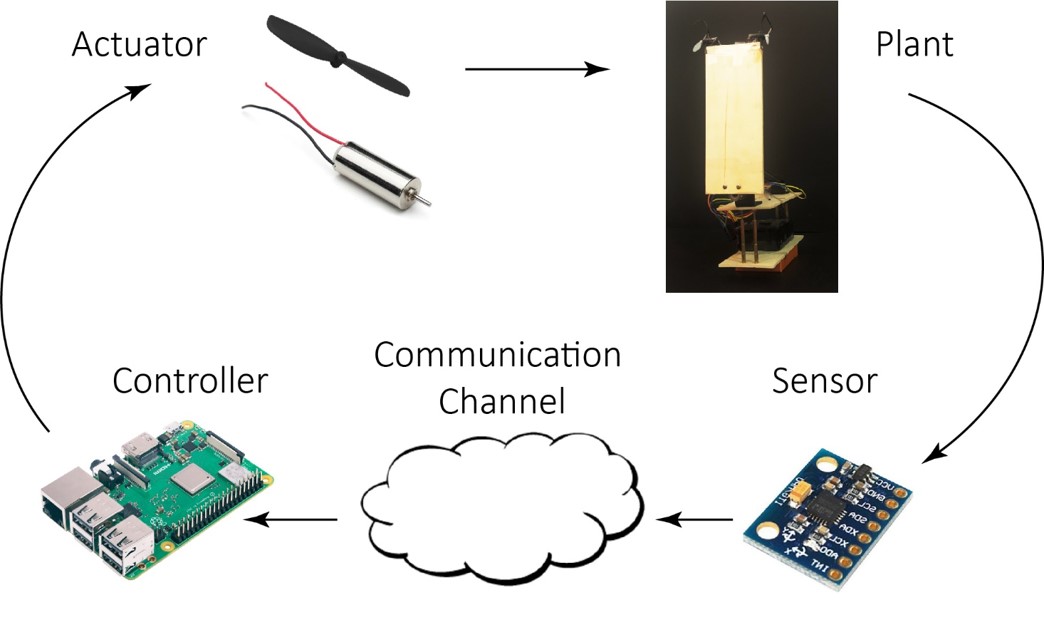
Recent technological advances in networking, communication, and computation technologies have enabled the development of cyber-physical systems and cloud robotics, where computing, communication, and control are tightly coupled and integrated into a single distributed platform. In most of these systems, the feedback loop is closed over a communication channel. In this context, we study event-triggering strategies that utilize timing information by transmitting in a state-dependent fashion. Compared to the conventional time-triggering setups, the proposed event-triggering strategies utilize the available communication resources more efficiently.
Selected publications:
- Information Flow in Event-Based Stabilization of Cyber-Physical Systems
- Exploiting Timing Information in Event-Triggered Stabilization of Linear Systems with Disturbances
- The Value of Timing Information in Event-Triggered Control
- The Many Facets of Information in Networked Estimation and Control